Understanding Cyber Security
Security awareness and an understanding of cyber security is steadily becoming a number one priority for many businesses across Australia and throughout the world. Being able to understand, predict, and plan for cyber security vulnerabilities and attacks on your business is extremely important, so knowing where to start or what the next steps are will be key to the successful continuation of operation your business.
While most businesses have at least a basic understanding of what cyber security is, due to the ever-changing landscape of attacks, and the global shift in the past 12-18 months to a remote and online workforce, managers and executives must keep abreast of these changes and understand how to integrate proper security awareness training and mitigation within their business. 2020 saw the continual rise in ransomware attacks of individuals and businesses, where attackers focussed on hijacking user endpoints and servers to extort money from their victims, causing massive financial and operational damage to those involved. However, businesses can take steps to help mitigate risks when it comes to ongoing security awareness and these and other kinds of potential attacks. While no one set of mitigation can completely protect you from future attacks, the Federal Government has created a set of strategies known as The Essential Eight to help businesses take the first steps in protecting themselves and educating staff on the importance of process and security awareness.
The ASD Essential 8
The Essential Eight are a set of mitigation strategies that are mainly focussed on businesses that are using Microsoft, Windows-based infrastructure and applications. While these strategies can be applied to other operating systems and applications, businesses must also plan and put into action other mitigation for security threats that are unique to their systems and hardware. The application of The Essential Eight strategies is based on a maturity level, indexing businesses into one of three levels. With each increasing level, the eight respective strategies require additional steps to help minimise the level of risk.
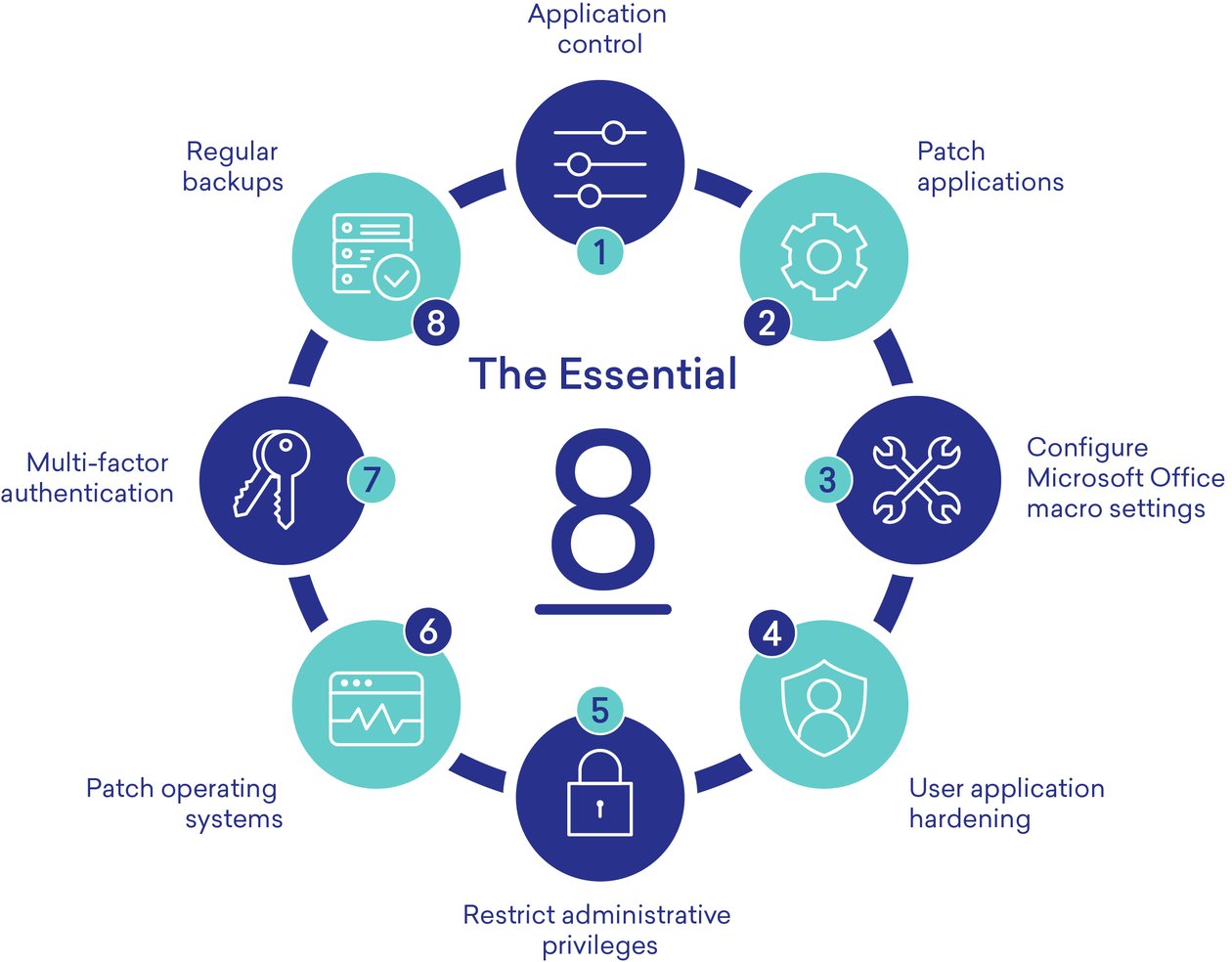
The Essential Eight Maturity Model can be examined in more detail on the ASCS website (https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-maturity-model) to gain a greater understanding of what level your business fits into and what specific steps need to be taken. However, the eight mitigation strategies at their core are the same across all maturity levels, which are:
- Application control
- Patch applications
- Configure Microsoft Office macro settings
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication; and
- Regular backups
While these strategies aim to help businesses prepare and minimise threats, it must be noted that the Essential Eight outlines a minimum set of preventative measures. Businesses must also look into implementing further measures where necessary, based on their industry, environment, infrastructure, etc. Again, no set of measures can fully protect any given business or organisation, but The Essential Eight is an excellent point to start at, or review to ensure you’re following the measures as closely as possible.
Truis understands security. We work closely with our vendors, and we have our own security specialists on staff to ensure our clients are getting the right security awareness training, assistance, and analysis needed to help them prepare their business for what the future might hold. We can help you navigate this tricky journey, managing everything from endpoints through to servers, and even help your staff with their security awareness with phishing training – one of the most common attacks on businesses.
Check out more of our insights
ISO 27001 and ISO 9001: How ISO standards help IT managers
Being able to understand, predict, and plan for cyber security vulnerabilities and attacks on your business is extremely important, so knowing where to start is the key to any successful business.
Read articleIlluminating cybersecurity blind spots
Being able to understand, predict, and plan for cyber security vulnerabilities and attacks on your business is extremely important, so knowing where to start is the key to any successful business.
Read articleFinding the right fit: E8, NIST CSF, or ISO 27001?
Being able to understand, predict, and plan for cyber security vulnerabilities and attacks on your business is extremely important, so knowing where to start is the key to any successful business.
Read article




